Security Assessment
What is a cybersecurity risk assessment?
A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization's IT environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences.
In most cases, a risk assessment will also provide recommendations for additional security controls to address the organization's specific challenges and mitigate the risk of breaches or other disruptive incidents.
Cybersecurity Security Assessment
A cyber security risk assessment is the process of identifying, analysing and evaluating risk. It helps to ensure that the cyber security controls you choose are appropriate to the risks your organisation faces. Without a risk assessment to inform your cyber security choices, you could waste time, effort and resources.

How To Perform a Cybersecurity Risk Assessment

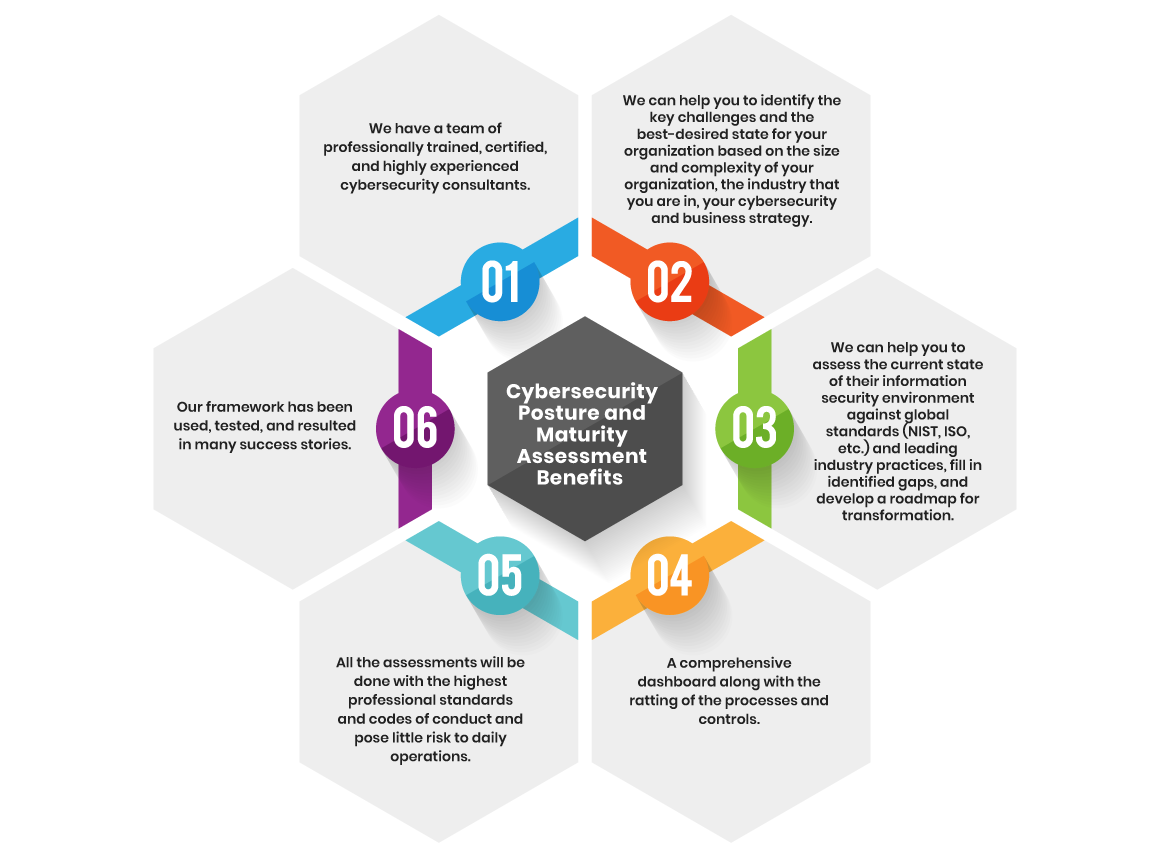


What is a cybersecurity risk assessment?
A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization's IT environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences.
In most cases, a risk assessment will also provide recommendations for additional security controls to address the organization's specific challenges and mitigate the risk of breaches or other disruptive incidents.
Importance of a cybersecurity risk assessment
Almost every modern business maintains an online presence and utilizes connected devices in its operations. This makes them vulnerable to cyberattacks, as any endpoint or online activity on any system can provide a gateway to threat actors looking to access systems, applications, data, and other assets.
Benefits of a cybersecurity risk assessment
The most obvious benefit of a cybersecurity risk assessment is to enhance the organization’s security posture across the entire IT environment. This is achieved through:
Improved visibility into IT assets and applications
A complete inventory of user privileges, activity within Active Directory, and identities
Considerations before performing a cybersecurity risk assessment
Before conducting a cybersecurity risk assessment, organizations should take several preliminary steps to ensure they are prepared for success.
Set clear objectives for the assessment.
Define the scope of the assessment.
Identify the assessment team.
Develop an assessment framework.
7 steps to perform a cybersecurity risk assessment
1. Perform a data audit and prioritize based on value
2. Identify cyber threats and vulnerabilities
3. Assess and analyze associated risk
4. Calculate the probability and impact of different cyber risks
5. Implement security controls
6. Prioritize risks based on a cost-benefit analysis
7. Monitor and document results
Why Choose IP Care Technologies?
Great Combo
- Our hybrid solution is like having the best of both worlds – cloud mail and M365 – to make your business even better.
Good Prices
- We don't want you to spend too much. Our plans are affordable so you can get the best tools for a good price.
Easy Switch
- If you're worried about changing, don't be. Our team will help you step by step, so you won't have any problems.
Made for You
- Your business is special, and we know that. Our plan will be just right for what you need.
