Privileged Access Management (PAM)
Why Privileged Access Management Is Needed?
Privileged access management solutions are crucial to protecting the privileged accounts that exist across businesses’ on-premises and cloud environments. Privileged accounts often hold the key to confidential and sensitive information that can be hugely damaging for organizations if they fall into the wrong hands.
It is easy for organizations to overprovision account privileges to resources that do not need them. Some users also end up accumulating new privileges or retaining privileges they no longer need when their job role changes. This privilege excess, in addition to the growth of cloud adoption and digital transformation, can lead to the organization’s attack surface expanding.
What is privileged access management (PAM)?
Privileged access management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized privileged access to critical resources. PAM works through a combination of people, processes, and technology and gives you visibility into who is using privileged accounts and what they are doing while they are logged in. Limiting the number of users who have access to administrative functions increases system security while additional layers of protection mitigate data breaches by threat actors.

Four Key Steps for Effective PAM Implementation
Identify Privileged Accounts
-
The first and most important step is to audit and identify all the privileged accounts that exist in your IT environment
Identify Sensitive Assets And Data
-
The next stage is to identify what sensitive data and assets your privileged accounts might be accessing.
Remove Unnecessary Access
-
Once you’ve identified both privileged accounts and sensitive assets, the next stage is to implement least privilege.
Implement Modern PAM Protections
-
Removing unnecessary privileges is a great first step – but it’s not the only tool in your arsenal. After all, there will always be accounts that need access to sensitive information.
What Is Privileged Access Management (PAM)
Privileged access management (PAM) is a crucial aspect of cybersecurity that focuses on securing and managing an organization’s privileged accounts. Privileged accounts have elevated access rights and permissions to the organization’s critical IT systems and applications. They allow users to perform administrative tasks to those systems.



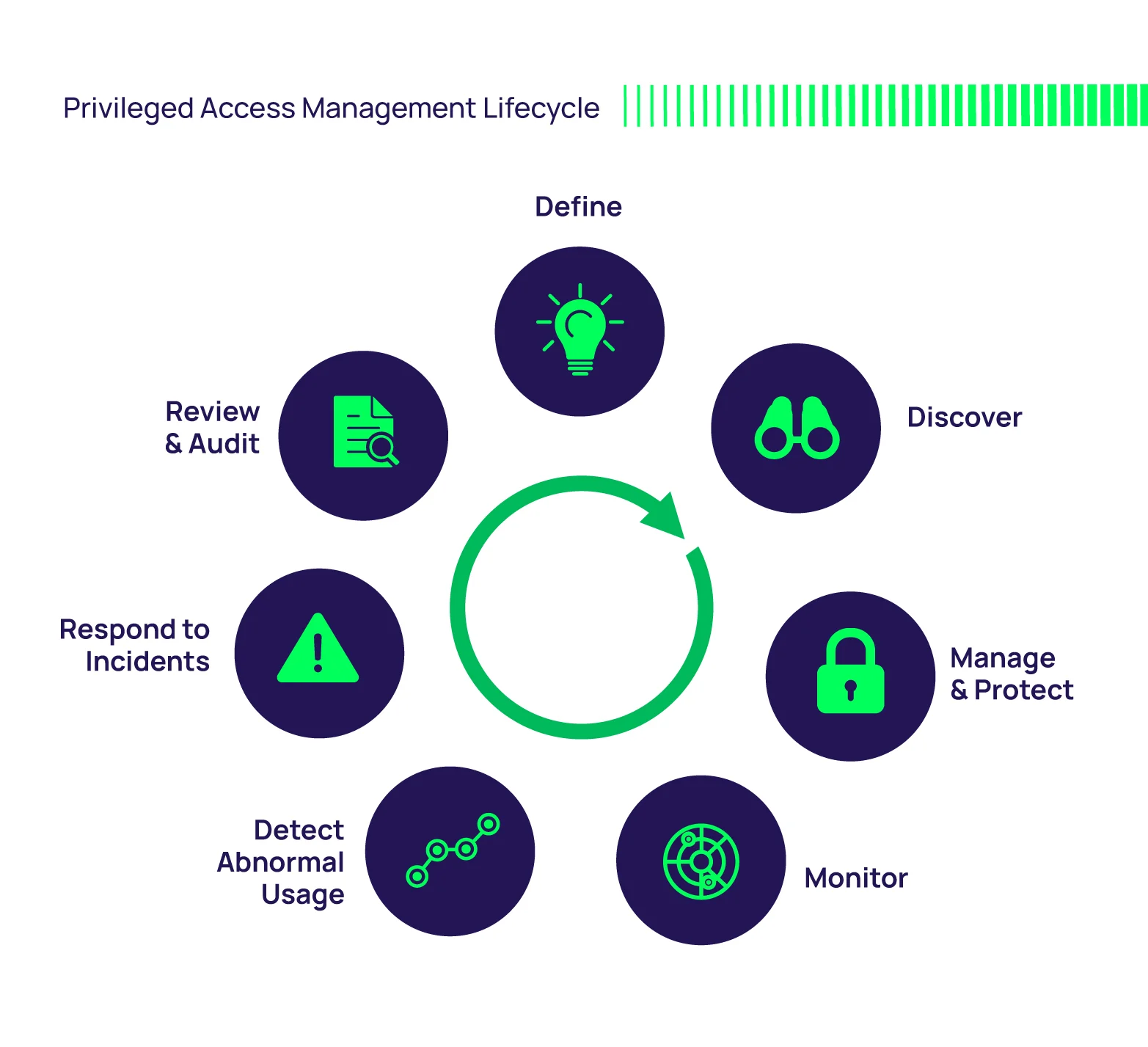
How Does PAM Work?
PAM systems provide a platform for a cybersecurity strategy to control, monitor, secure and audit all human and non-human (service accounts) privileged identities and activities across an enterprise IT environment. It enables a combination of people, processes and technology to help organizations protect against the threats posed by credential theft and privileged account misuse.
What Are Privileged Accounts?
At the core of PAM lies the concept of “privileged accounts,” which are essential to controlling and maintaining security in today’s information systems. Privileged accounts are granted greater control and permission levels than standard user accounts. They have the authority to access, modify or manage critical resources, such as user accounts, databases, network devices, servers, applications and more. The two most fundamental forms of privileged accounts are user and machine accounts:
1. User accounts. User accounts refer to accounts assigned to individuals with specific organizational roles. These roles often include different types of administrators, IT and otherwise, and other employees who require administrative access.
2. Machine accounts. Machine accounts are associated with systems or services used for automated processes or communication between integrated systems. These accounts typically do not have human users.
Types of Privileged Accounts
Privileged accounts, often called administrative accounts, come in many forms and offer varying levels of administrative power. Some of the most common types of privileged accounts include:
1. Domain admin
2. Local administrator
3. Non-human automation
4. service
5. Root
6. Network equipment
7. Firwall
8. Database administrator (DBA)
9. Cloud service provider (CSP)
There’s no substitute for switching to data infrastructure designed for the modern era. FlashBlade delivers Rapid Restore for production and dev/test workloads with up to 270TB/hr of data-recovery performance.
Best Practices of Privileged Access Management
IPAM is integral to securing an organization’s critical information and resources. However, employing best practices is vital in ensuring an effective PAM strategy and protecting privileged accounts against cyber threats. Here are some of the core best practices of any privileged access strategy.
1. Implement the principle of least privilege (PoLP)
2. Assess privileged accounts based on risk
3. Write a formal privileged account password policy
4. Implement just-in-time access
5. Configure and review user access rights
6. Establish effective account life cycle processes
7. Periodically audit the configured privileges
Notable Security Breaches Involving Privileged Access
Over the past decade, there have been numerous security breaches linked to privileged access abuse. From Terry Childs and Edward Snowden to Yahoo! and the massive breach at the U.S. Office of Personnel Management to the Bangladesh Bank breach and the attack on the Ukraine power grid and even the highly publicized Uber breach – the common denominator in each attack was that privileged credentials were exploited and used to plan, coordinate and execute cyber attacks.
Why Choose IP Care Technologies?
Great Combo
- Our hybrid solution is like having the best of both worlds – cloud mail and M365 – to make your business even better.
Good Prices
- We don't want you to spend too much. Our plans are affordable so you can get the best tools for a good price.
Easy Switch
- If you're worried about changing, don't be. Our team will help you step by step, so you won't have any problems.
Made for You
- Your business is special, and we know that. Our plan will be just right for what you need.
